AnyConnect VPN Correlation Rule Pack - Part 2.
OK. Lets proceed further. The part 2 of the write up will dig into the correlating more information. In my setup ASA is giving out the internal IP addresses to the successfully authenticated user based on the profile assigned to the username.
What I will try to do is correlate three events to record source public IP, internal DMZ IP, NAS Port, user policy and user name.
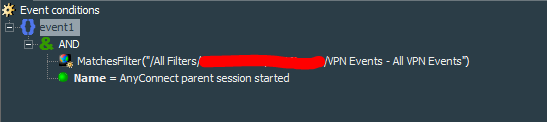
Lets create filter VPN Events - VPN AnyConnect parent session started that would catch events with the name = “AnyConnect parent session started” and match the filter VPN Events - All VPN Event.
Another one will be VPN Events - ACS Successful Authentication and it would catch events with the name = “Authentication succeeded” and deviceAddress = IP Address of the ACS and match the filter VPN Events - All VPN Event.
Inspect the events to understand how to correlate.
- “AnyConnect parent session started” event has destinationUserName as the user name and destinationAddress as the public IP address.
- “RADIUS Accounting start request” event has desitnationUserName as the user name, sourceAddress as the internally assigned IP address and the deviceCustomString2 as the NAS port.
- “Authentication succeeded” event gives has destinationUserName as the user name and the deviceCustomString3 as the policy name.
With these filters set we are ready to start creating the correlation standard rule VPN Events - AnyConnect Session Established. For the conditions create three events called ACSSession, AnyConnect and ACSAuth matching filters as per table
| Event Name | Filter Name |
|---|---|
| ACSSession | VPN Events - ACS Session Start |
| AnyConnect | VPN Events - VPN AnyConnect parent session started |
| ACSAuth | VPN Events - ACS Successful Authentication |
I set Consume after match flag for all the events, because it prevents the rule from generating identical correlation events.
Create Matching Event with matching time equal to 30 seconds where ACSSession.Target User Name = AnyConnect.Target User Name and AnyConnect.Target User Name = ACSAuth.Target User Name.
Next we will create four local variables that would alias event fields.
| Variable Name | Eventr Field |
|---|---|
| extAddress | targetAddress |
| intAddress | attackerAddress |
| profileName | deviceCustomString3 |
| nasPort | deviceCustomString2 |
After variables creation we shall proceed to the aggregation and it should match 1 event per 30 seconds with identical fields ACSSession.nasPort, ACSAuth.profileName, ACSSession.intAddress, ACSAuth.Target User Name, AnyConnect.extAddress_
Finally we need to assign some actions. I do it On Every Event and set the event fields as follows:
- message = “AnyConnect Session Established”
- categoryDeviceType = “VPN”
- categoryBehaviour = “/Access/Start”
- categoryDeviceGroup = “/VPN”
- categoryObject = “/Host/Application/Service”
- categoryOutcome = “/Success”
- categorySignificance = “/Informational/Warning”
- attackerAddress = $extAddress
- deviceCustomString3 = $profileName
- deviceCustomString4 = $nasPort
- destinationTranslatedAddress = $intAddress
Thats it. If everything goes well, after deploying the rule to the Real-Time processing it should start generating the event that would collect 3 base events and set the fields as configured above.
Mentions
Photo by Gabriel Crismariu on Unsplash